Main bulk encryption algorithms used in commercial applications. AES is one example of such algorithm.
Principles
Block ciphers are symmetric key ciphers where each block of plaintext encrypted with the same key.
A block is a set of plaintext symbols of a fixed size, typically 64 to 256 bits in modern ciphers.
They are used in configurations called modes of operation.
Notation
-
: plaintext block of length bits -
: ciphertext block of length bits -
: key of length bits - Encryption:
- Decryption:
Criteria
Shannon defined two encryption techniques:
- Confusion: substitution used to make the relationship between
and as complex as possible. - Diffusion: transformations used to dissipate the statistical properties of
across .
Repeated use of techniques can be used using the concept of a product cipher.
Product & Iterated Ciphers
Product Cipher
Cryptosystem where encryption performed by applying/composing several sub-encryption algorithms: output of one block used as input to next block.
Often composed of simple functions
Iterated Cipher
Special product ciphers called iterated ciphers where:
- Encryption divided into
similar rounds - Sub-encryption functions are the same function
: the round function - Each round key/subkey
is derived from the master key using a process called key schedule
Encryption
Given plaintext block
Decryption
There must be an inverse function
Types of Iterated Ciphers
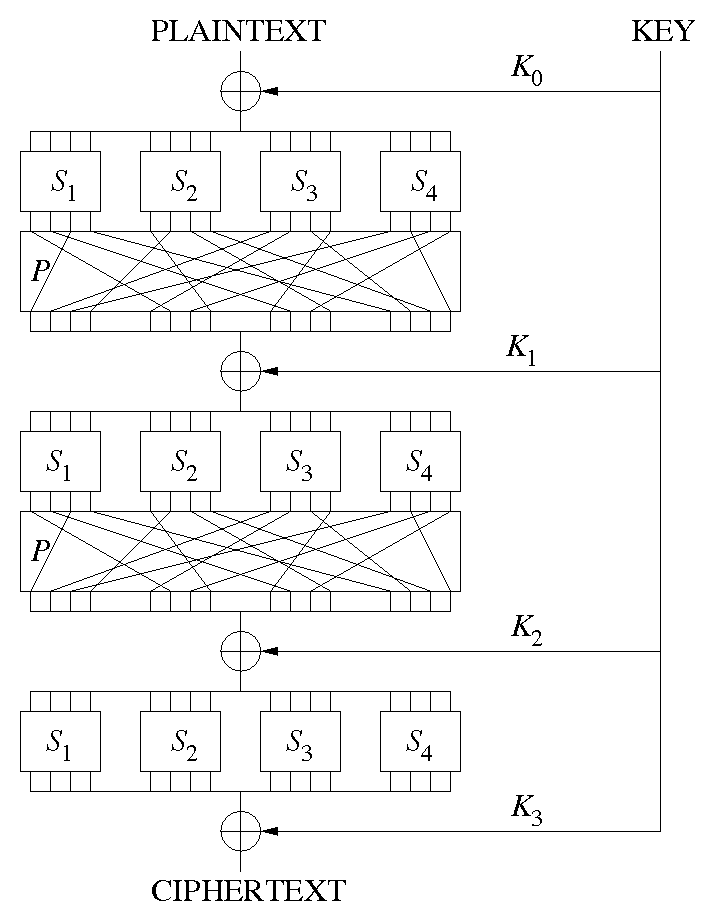
Substitution-Permutation Network (SPN) e.g. Advanced Encryption Standard (AES).
Feistel Cipher e.g. Data Encryption Standard (DES).
Substitution-Permutation Network
Block length
Substitution
i.e. mapping some binary number of size
Permutation
i.e. swapping the order of bits in the entire block around.
Operation
- Round key
XORed with current state block : - Each sub-block substituted applying
- The whole block permuted using
Example
- 4 round keys
- 4 S-boxes
- 1 P-box
- Last round does have a P-block
Feistel Cipher
Round function swaps the two halves of the block to form a new right hand half.
Encryption
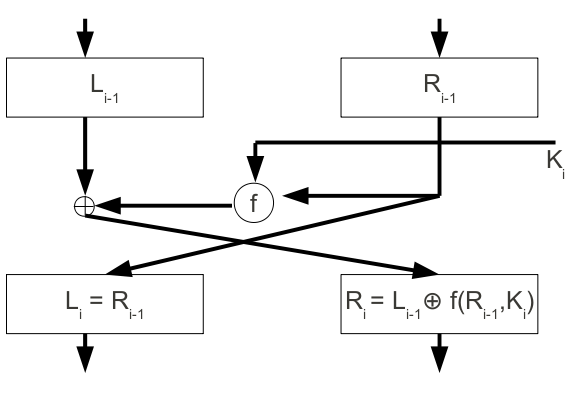
Plaintext block
For each round:
The output is the ciphertext block
Decryption
Split
For each round:
The choice of
Differential and Linear Cryptanalysis
Differential cryptanalysis: chosen plaintext attack using correlation in the differences between two input plaintexts and their corresponding ciphertexts.
Liner cryptanalysis: known plaintext attack that theoretically break DES.
Modern block ciphers normally immune to both attacks.
Avalanche Effects
Key avalanche: a small change in key (with the same plaintext) should result in a large change in ciphertext.
Plaintext avalanche: a small change in plaintext should result in a large change in ciphertext: changing one bit should change all bits in the ciphertext with a probability of
Key avalanche is related to Shannon’s notion of confusion, plaintext avalanche to Shannon’s notion of diffusion.
DES
Designed by IBM researchers, became US standard in 1976. 16-round Feistel cipher with key length of 56 bits and data block length of 64 bits.
The key length is actually 64 bits, but the last bit of every byte is redundant.
Encryption
- All bits of
permuted using an initial fixed permutation of - 16 rounds of Feistel operations applied, denoted by function
- Each round uses a different 48-bit subkey
- The subkey is defined by a series of permutations and shifts
- A final fixed inverse permutation
is applied
The 64-bit ciphertext block
Decryption requires only reversing the order in which the subkeys are applied.
Feistel Operation
- 32 bits expanded to 48 bits using a padding scheme which repeats some bits
- XOR the 48 bits with the 48-bit subkey
- Break 48 bits into 8 blocks of 6 bits
- Each block
transformed using substitution table , resulting in blocks of length and hence a total of 32 bits. - A transformation table is used to determine the output value
- If the input block is
, the row number is given by and the column number by
- A permutation is applied to the result
Brute Force Attacks
Testing all the possible
The key can be identified by using a small number of ciphertext blocks and looking for low entropy in the decrypted plaintext.
Double Encryption
Let
Encryption:
If both keys have length
Meet-in-the-Middle Attack
Let
- For each key
, store in memory - For any key
, check if (i.e. matches any ciphertext stored in memory) - If this is found,
is and is - Check if key values work for other
pairs
- If this is found,
Requirements:
- Storing one plaintext block for every key:
64-bit blocks - An encryption operation for every key
- A decryption operation for every key
Expensive but still much cheaper than brute-forcing
Triple Encryption
Requires three keys:
This increases the computational requirements enough to make it secure against MITM attacks.
NIST SP 800-131A (2015) approves two-key triple DES, where
OpenSSL removed triple DES in 2016. Office 365 stopped using triple DES in 2018.
AES
Designed in an open competition after controversy over DES. Winning submission is ‘Rijndael’.
- 128-bit data block
- 128-, 192- or 256-bit master key
- Byte-based design
- Substitution-permutation network
- Initial round key addition
- 10, 12, or 14 rounds (depending on key size)
- Final round
Algorithm
State Matrix
16-byte data block size arranged in a
Mixture of finite field operations in
Round Transformation
Each round has four basic operations:
- ByteSub (non-linear substitution): substitute each byte wth a different value using a substitution table
- ShiftRow (permutation): rotate first row right by zero bytes, second row right by one byte… (bytes wrap to left)
- MixColumn (diffusion): each column is replaced with result of it being multiplied by a matrix
- AddRoundKey: XORs array with round key
Substitution-permutation network with block length of
S-box uses look-up table.
Key Schedule
Master key is 128/192/256 bits.
Each of the 10/12/14 rounds uses a 128-bit subkey. There is one subkey per round plus one initial subkey, all derived from the master key.
Security
Some weaknesses but no significant break; most serious real attacks can reduce effective key size by around two bits.
Vulnerable to related-key attack: attacker obtains a ciphertext encrypted with a key related to an actual key in a specified way.
Comparisons with DES
- Data block size: 64 vs 128 bits
- Key size: 56 vs 128/192/256 bits
- Design:
- Both iterated ciphers
- DES uses Feistel; AES uses SPN
- AES substantially faster in both hardware and software